The mission for Banyan Security Service Edge (SSE) has been the same since day one; enable the modern workforce to securely, safely, and easily access the applications and services they need, while working from anywhere. This means the good guys get access to what is needed, and the adversaries get access to nothing.
With today’s computing being truly perimeter-free, this is a challenge, since organizations don’t have 100% control over their data storage or application systems. Moreover, remote employees and contractors may be in coffee shops, airports, and homes accessing internal applications running in multiple public clouds, connecting to other cloud applications and enterprise data centers. Mobility, containers, and public and private clouds have unleashed innovation like never before, as well as unique security challenges.
Our job is to ensure that the ROI for attacking us or our customers doesn’t make sense for adversaries, and that they need to look elsewhere for an easy target. Look at it from the perspective of the attacker’s wallet: an attack has overhead costs that attackers incur when launching their plans, just like legitimate businesses. These costs can include acquiring or developing hacking tools, conducting reconnaissance, hiring skilled individuals, participating in cybercrime forums, and maintaining infrastructure like command-and-control servers. All of this must be staffed and automated (and people and tools cost money). Additionally, attackers may need to invest in techniques to obfuscate their activities and evade detection. These attackers are motivated by various factors, such as financial gain, political motivations, espionage, or simply causing disruption. The potential gains can include stealing sensitive data, accessing financial information, extorting victims, disrupting operations, or gaining a competitive advantage. Attackers may monetize the stolen data by selling it on the dark web or using it for identity theft or blackmail.
Let’s be honest, hacking organizations is getting easier in some ways, especially in the age of ChatGPT spearphishing or other AI-driven attacks. Weak cybersecurity measures, including inadequate passwords, lack of encryption, unpatched software, absence of multi-factor authentication, and insufficient network security controls, make organizations vulnerable to attacks. Inadequate employee awareness and training in cybersecurity best practices contribute to successful social engineering attacks. Organizations with insufficient incident response capabilities struggle to detect and respond effectively to breaches. Complex IT infrastructure poses challenges in securing systems, while limited resources and budget constraints hinder cybersecurity initiatives. Additionally, third-party risks introduce vulnerabilities. While determined attackers can breach any organization, addressing these vulnerabilities and implementing robust cybersecurity practices significantly reduces the risk and makes it more difficult for attackers to exploit systems and data.

Understanding the economics of cybersecurity attacks helps us develop strategies to allocate resources effectively and prioritize investments in prevention, detection, and response to mitigate the risks associated with cyber threats. And since one should also plan for when an attack is successful, Banyan’s SSE solution should also limit the damage and allow for forensics.
Reducing the Attack Surface for Adversaries
Reducing the attack or threat surface is usually step one. All corporate resources, data, and applications that do not need to public or reachable…shouldn’t be. This includes documentation and instructions that can possibly be used for social engineering. Also, this assumes that the attacker is an outsider. For internal bad actors or just unwitting employees, the introducing of least privilege access (LPA) and east-west traffic controls are also important. Software that is running on the insider’s computer may be doing thing that the insider isn’t even aware of, making them an “accidental insider.”
Banyan’s approach to reducing the attack surface can be seen in many ways. This includes the microservices we deploy for our own SSE solution along with all of the customer premises software we deploy (such as the connector.) The Banyan connector is only communicating outbound: it’s not exposing DNS names, external IP addresses, or pin-holing ports on the firewall. As far as outsiders are concerned, the connector doesn’t exist. Banyan also ensures that policies are LPA, meaning that even known users on known and compliant devices can only access the bare minimum applications, resources, and data needed to get their work done.

Brute Force Attacks
To counter brute force attacks and unauthorized access attempts, several measures can be taken to enhance system security. These include implementing strong password policies, enabling account lockouts, utilizing multi-factor authentication (MFA), rate limiting and delaying login attempts, monitoring and analyzing login activity, deploying intrusion detection/prevention systems (IDS/IPS), employing account lockout policies, using CAPTCHA or challenge-response mechanisms, regularly updating and patching systems, and conducting security awareness training. By implementing these measures, the risk of successful brute force attacks can be significantly reduced, strengthening overall system security and staying ahead of evolving threats.
Banyan’s solution can remove the password completely, which enhances security and provides a better end user experience. Passwords become an issue for organization especially when policies require changing passwords frequently. By using passwordless authentication policies, credentials that are acquired on the dark web are useless.
SIM Swapping
To prevent SMS attacks following a SIM swap, it is important to take proactive steps to protect your accounts and enhance mobile number security. These steps include using strong and unique passwords, implementing alternative 2FA methods like app-based authenticators or hardware security keys, utilizing app-specific passwords where possible, installing mobile security apps with SIM card change alerts, setting a PIN/password for your mobile account, enabling account notifications and alerts, contacting your mobile service provider if you suspect a SIM swap, monitoring account activity, being cautious of phishing attempts, and maintaining device security. By implementing these measures, you can reduce the risk of SMS-based attacks and ensure the ongoing security of your accounts and data.
Banyan’s solution allows for multi-factor authentication. This is beyond your standard two-factor authentication (2FA). By using certificates, along with system information, and combining then push notifications or one-time time-based passcodes, organizations can disable all SMS-based authentication methods to completely prevent SMS-based leaks and attacks.
To mitigate social engineering attacks and minimize the risk of successful hacking, organizations should implement the following measures: educate employees on social engineering tactics and promote skepticism, enforce strong password policies and implement multi-factor authentication, develop and update an incident response plan, conduct security awareness campaigns and encourage reporting of suspicious incidents. This will go hand-in-hand with the deployment of email and web filtering solutions. IT organization should also regularly update software and apply patches to prevent the use of known vulnerabilities. These measures enhance defenses against social engineering attacks, but it’s crucial to remain proactive and informed about evolving tactics used by attackers.
Banyan’s approach of using MFA, third-party inputs, and device-specific information to come up with a Trust Score means that even if an attacker happens to get a username, password, and MFA token, they still don’t have enough information to access a machine. Banyan’s security service edge (SSE) solution knows that the access request isn’t coming from the correct end user device.
Banyan further protects against phishing with our Internet Threat Protection (ITP) capabilities, ensuring that even when employees attempt to click on links that lead to bad sites, the connection is intercepted and not allowed. This protect also stops connections to command-and-control servers.
Logging and Forensics
Logging is vital for post-breach forensics as it provides valuable insights into network and data security breaches. To leverage logging effectively after a breach, organizations should take the following steps: preserve and secure logs by restricting access, making backups, and preserving relevant network device and server logs. It is also necessary to establish a logging policy aligned with industry best practices and regulatory requirements as well as analyze logs for indicators of compromise by identifying abnormal or suspicious activities and creating a timeline of events. Most organizations will utilize SIEM and log analysis tools to automate log analysis, identify patterns, and determine the scope of the breach. More advanced organizations conduct timeline reconstruction to identify the root cause, affected systems, and potential data exfiltration or tampering. Tools that identify compromised accounts or credentials by analyzing authentication and access control logs and correlate log data with external threat intelligence to identify known malicious entities may also be required. It’s important to recognize that log analysis is just one aspect of a thorough forensic investigation.
Banyan SSE vs the Adversaries
Banyan’s app and administrator console collect lots of logs for processing by Banyan or using your organizations SIEM. The logs include granular details that will provide digital forensic researchers valuable insights into system activities, user actions and device state, network traffic, and other events that may be relevant to an investigation. Logs can be exported in different formats to easily be used without needed to be converted using another tool.

To learn more about why adversaries hates and to see why administrators (and end users) love us, schedule a custom demo today or attend our weekly live demonstration.
The post Why Adversaries Hate Banyan SSE first appeared on Banyan Security.]]>
Device trust? Geek-speak for “how safe is your device,” device trust is foundational to the security of an organization and its users. As a counterpoint, there’s device shame: you don’t want to be the one to introduce a problem into the organization. Also, for most users, the computer they use for work also has a lot of personal information or files on it, for example, family pictures and other documents that were downloaded during the course of the workday. Having a device with low trust levels looks like this: any place you visit, and then access the network is a nexus from which serious issues can spread. And with the right amount of logging and forensic information, this activity can be traced back to you. This is why having a trusted device is the cornerstone to a robust security strategy.
To give you an idea of scale of the global problem with low trust levels, statistics suggest up to 900 million unpatched Windows machines with vulnerabilities that can possibly be breached. Also, just on Android, over 550 vulnerabilities were found in 2021, and malware was present on over 10 million mobile devices (including iOS). Finally, according to Ironscales’ State of Cybersecurity Survey, phishing emails have become more frequent. Since the start of the pandemic in 2020, 81% of global organizations have reported more email phishing attacks. So what can be done and why do end users care?
Looking at the below Banyan app we can see there are a few things that we calculate our trust levels on. There are more factors than the below but in this blog we’ll just look at what Banyan looks at directly and the types of information that we can get from some of our EDR partners such as Crowdstrike and SentinelOne.
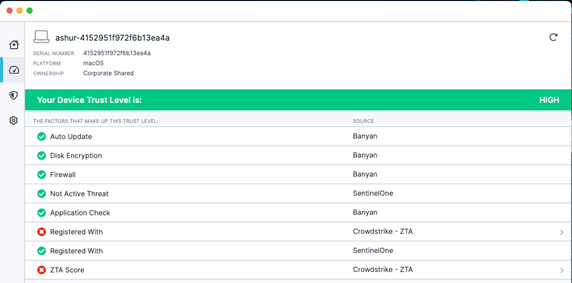
The four standard Banyan App factors include:
1. Auto Update
Ensures that the end user device is always running the latest and greatest operating systems which includes security updates.
2. Disk Encryption
Ensure that disk encryption is configured to help protect any intellectual property (IP) that is on the device in case the device is stolen or lost.
3. Firewall
Ensures that on-device software firewall is configured. The default configuration for the firewall usually includes blocking all inbound connections as well as blocking ICMP replies which are used for ping tests looking for systems to attack. This will also keep the system details invisible from Nmap and other scans.
4.Application Check
Ensures that the required, corporate-issued security software is installed and running, along will checking for undesired or malicious software that is installed. Some software, such as Metasploit, may be used by bad actors doing bad things, or penetration testers checking system security. Many times, these get flagged, and administrators need to whitelist systems that have a reason to have these types of software.
More factors as well EDR integrations are available and can be configured, either in visibility or enforcement mode.
Endpoint Detection and Response (EDR) integrations are important. The typical use case is that the EDR agent is installed on an end user device, a policy is configured on the EDR, and a score or compliance state is sent to the SSE/ZTNA solution. This is similar with MDM/UEM. How this score or compliance state is calculated depends on the vendor. These integrations are quickly configured using an API URL and a token for authentication.
SentinelOne sends over information about agent installation and state as well as flagging for active threats. Remediation can happen using instructions along with functionality built into the SentinelOne app such as the quarantine of malicious files.
The Crowdstrike Zero Trust Assessment (ZTA) delivers real-time security posture assessments across all endpoints regardless of location, network, and user. Falcon ZTA enables enforcement of dynamic conditional access based on device health and compliance checks that mitigate the risk to users and the organization. Every endpoint is granted least privileged access and is assessed before gaining access to sensitive data and corporate assets – ensuring Zero Trust enforcement across all endpoints. By expanding Zero Trust beyond authentication and including device security, CrowdStrike Falcon ZTA helps organizations maintain a holistic cybersecurity approach that protects their data and users from the sophisticated tactics of cyber adversaries.
With the recently announced acquisition of Preempt Security, CrowdStrike has advanced its Zero Trust capabilities to achieve end-to-end, real-time visibility and granular enforcement with advanced conditional access technology for real-time access control and threat prevention. The new capabilities will help unify identity and workload-centric conditional access capabilities with the CrowdStrike Falcon protection suite to help secure users, workloads, and data, regardless of location and network and without modification to existing legacy infrastructure and operating systems.
To learn more about how Banyan ensures device trust for your network, attend our weekly live demo or schedule a custom demo today.
The post Why End Users Actually Care About Device Trust first appeared on Banyan Security.]]>
On April 4th, 2023, we announced our expanded device-centric Security Service Edge (SSE) solution. From company inception, we decided that an approach to access and security built devices outward provided the biggest advantage to our customers. In this blog, we’ll take a look at why we took a device-centric approach in architecture, and highlight some pitfalls with other popular approaches.
What Does Device-Centricity Mean?
Let’s look at a few “centricities.” These are based on other, well-known vendors in the security world and come directly from their webpages:
- App-centric: App-centric, in this case, means lots of interaction with an app before anything happens. (Data-centric implies that that all the traffic must go to the vendor to be inspected.) Most of the app-centric vendors only work after a user has logged in to the application.
- Data-centric: This approach may work when data integrity is your primary concern, and the data lives in one place, say on-premises. However, when data is distributed, this approach is very difficult to achieve. This is especially hard when applications and resources are in third-party SaaS environments.
- User- and Identity-centric: Minimizes the details going from what (the device), and from where (the end-user location or device).
- Cloud-centric: This is basically the same as data-centric, meaning where the information lives, minimizing on-premises and SaaS. Also, minimizes the who, from what, and from where.
- Human-centric: High BS rating for this one, and it’s surprisingly findable in marketing copy from other cybersecurity companies. Possibly the hardest, least-predictive part of the information ecosystem. This ignores behavior on the system that the “human” isn’t even aware of.
- Identity-centric: Minimizes the device, which is evident in the products and lack of device identity and compliance functionality. Asking for more detail on identity often seems to introduce confusion, and reveals the product over-promises what can be delivered.
- Everything-centric (data, customer, application, network): It’s hard to talk about an approach that lacks focus. This is more of a marketing messaging strategy, rather than an approach. One specific vendor that is pushing this approach wants all the traffic to go to them so not only are they “everything” centric, but they get to look all “everything” your company has, since all the traffic is forced to go through them to get decrypted and inspected (among other things).
Identity and Devices

While the Banyan platform integrates with many identity providers, and many of them have pivoted their messaging into a more holistic security story, knowing the shortcomings of the identity-based approach may help with your decision-making.
Identity-based security is an approach that focuses on verifying the identity of users (and possibly devices) accessing a system or network, and granting or denying access based on their identity. The following are some potential drawbacks to this approach:
- Increased complexity: Identity-based security can be more complex and difficult to implement than traditional perimeter-based security approaches, which focus on securing networks and endpoints. It requires a deep understanding of the organization’s identity landscape, including user roles and access rights, as well as the ability to manage and synchronize identity information across multiple systems and applications.
- Cost: Implementing identity-based security can be expensive, particularly for organizations that have large numbers of users or that need to comply with strict regulatory requirements. This can include costs associated with identity verification, access control mechanisms, and ongoing monitoring and management.
- User resistance: Identity-based security can be perceived as a burden by end-users, who may be required to provide additional authentication or follow specific procedures to access protected resources. This can result in user resistance and may require additional training and support to ensure compliance.
- False sense of security: While identity-based security can improve security, it is not foolproof and can create a false sense of security if not implemented properly. For example, if an attacker gains access to a user’s credentials or if a user’s account is compromised, the attacker can potentially bypass identity-based security measures.
- Single point of failure: Identity-based security relies on a centralized identity management system, which can create a single point of failure. If the identity management system is compromised, it can potentially grant unauthorized access to sensitive resources.
Though identity-based security can provide significant benefits, it is important to carefully consider the potential drawbacks and ensure that it is implemented in a way that is effective, efficient, and user-friendly. This may involve balancing the need for security with the need for usability and minimizing the risk of a single point of failure.

Smart Security Starts with Devices
So why device-centric security?
- The device is the new edge. This is especially true with more people working remotely.
- Moving security stack to the “new edge” makes sense, unless you want to backhaul or hairpin all the traffic back to corporate network to use legacy outbound security stacks. Which one sounds like more configuration and headache?
Devices Determine Everything
- Because we are device-centric, we don’t require an end-user to connect to our system to:
- validate device compliance/posture checks
- enforce device trust and real-time continuous authorization
- get easy, passwordless access (since we can do proxies and device certificate authentication).
- Because we are device-centric, users and devices get resources AND data privacy
- granting user/device access to resources behind a connector/access tier without sending traffic to Banyan.
- Because we are device-centric, we facilitate internet threat protection (ITP)/SWG/DNS filtering
- enforcing this on the device itself using an on-device proxy to our DNS filter.
Intelligent routing policies done on the client means that most of the traffic doesn’t have to be backhauled, and you can still enforce authentication, device identity/posture, and authorization. Moreover, you can ensure that all “public” (over-the-internet) communications are secured, even if the application and resources themselves don’t enforce security, authentication, or encryption.
Visit us here to learn more about the benefits of a device-centric approach and try Banyan for free.
The post Why Smart Cybersecurity Starts with Devices first appeared on Banyan Security.]]>
Device trust has come a long way, and is evolving even faster, stimulated by integrations and vendors that are developing device-centric solutions. But it wasn’t always this way… in the early networking days, a device that didn’t have a user (for example, a printer) would be put on a segmented network that wasn’t even secured. Anyone could unplug the printer, connect their computer, and get access to the network.
A brief history of device trust
This quickly became the weakest link in the network, so functionality like Network Access Control (NAC) and protocols like 802.1x were introduced. MAC authentication (what Cisco calls “mac auth bypass”) used a MAC address as username and password. Sadly, companies that had thousands of phones, printers, and other devices would have to manually enter each device. This was not ideal and took forever, often resulting in incorrect entries. This was followed by automated profiling based on mac address OUI (organizationally unique identifier). OUIs would identify the device to allow them to be automatically added to specific VLANs.
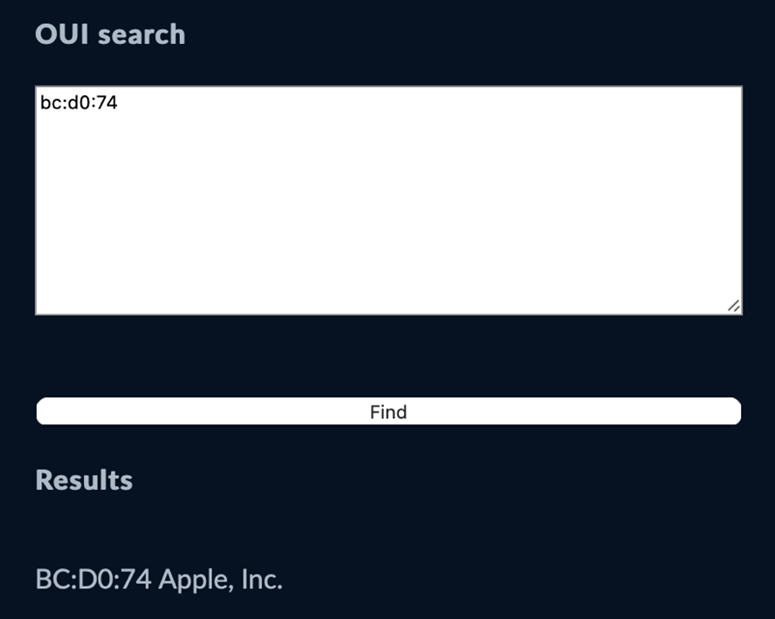
To quickly check out how OUI works, you can get the MAC address of the physical or Wi-Fi network interface and then check it against WireShark’s OUI lookup tool. Here’s an example of the (partial) MAC address of my MacBook:
Next on the scene: Internet of Things (IoT) and management server integration came along, and were useful to get extensive information on devices trying to connect to local networks, usually in manufacturing environments. As systems became more proprietary and didn’t support basic networking, they had management systems offering APIs or integration with systems that use standard protocols like RADIUS.
Both IoT and NAC protocols are helpful when dealing with on-premises and mostly fixed devices. So, what can be done for mobile and portable devices coming in from anywhere in the world?
So what is mobile device trust for?
Mobile device trust isn’t just for mobile devices like cellphones or tablets, but also for laptops. A solution should tie into mobile device management (MDM) and unified endpoint management (UEM) solutions that can be used to configure devices with zero-touch from the end user, as well as collect important device information that’s needed for certain types of compliance: how the device is configured, what applications are loaded on it, or location, for example.
Device identity is integral when creating a device trust policy. Device trust policies can be based on ownership type, such as corporate or customer-owned (in the case of BYOD). These policies can also be based on type (such as Apple or Android) or screen size, which may make connection types like RDP easier to use.
Device posture is just as important as identity. Device posture checks ensure that the device is in a state that the organization requires. This may include having the proper configuration, settings, and applications running. Device posture can also tie into endpoint detection and response (EDR) software for deeper inspection of traffic and applications which may detect malware and other unwanted software.
A word about UEBA
Knowing about the user on the device, the device itself, and the health state of the device is great, but a good user on a good device may still present a problem. That’s where User and Entity Behavior Analytics (UEBA) comes into the picture. Let’s take the example of discovering a company’s “business hours.” Most organizations may say business hours are Monday to Friday from 9am to 6pm, however, these business hours may not apply to software developers or devops folks that are working atypical hours pushing updates. The UEBA engine should create baselines for each user, and policies can be created to react when behavior is outside of the threshold of the learned behavior.
Having outdated device trust information is useless. Unlike other vendors that have lightweight device info, Banyan’s Device Trust is always-on; the effective changes to authorization based on device trust are real-time, happening almost instantly, resulting in the safest possible device-to-resource communication.
To learn more about how Banyan’s real-time Device Trust can help your organization deflect breaches, schedule a demo today.
The post Modern Device Trust for Today’s Advanced Threats first appeared on Banyan Security.]]>If it were an arm-wrestling match, it’s possible that Secure Access Service Edge (SASE) would beat Security Service Edge (SSE) if measured by bulk force alone. But if you’ve ever watched arm-wrestling (or any kind of wrestling), sometimes power and agility count for more than size and weight. In fact, in the last quarter of 2022, SSEs represented nearly 60 percent of the SASE market by revenue. The remainder, 40 percent, was SD-WAN…so it’s absolutely worth paying attention to that smaller, more agile player right now. While the secure access service edge and the security service edge definitely have overlap, they are suited to solve slightly different problems for the enterprise. Let’s take a look at which one you might need and when.
Where did the Secure Access Service Edge come from?
In 2019, Gartner recognized a new market segment for SASE and gave it a label: SASE is a network security architecture grouping SD-WAN, SWG, CASB, ZTNA and FWaaS as core abilities. SASE combines network security services with wide-area network (WAN) capabilities (like the SD-WAN software-defined wide-area networking mentioned above). SASE delivers network and security services from the cloud and aims to provide secure access to any application, regardless of where it is hosted.
SASE creates regionally distributed points of presence (PoPs) using a software-based virtual network; the PoPs provide nearby secure networking and cloud-based security functions to both branch offices and remote users. Bringing secure networking geographically closer to its users, SASE reduces lag and latency, vanishes the need for perimeter edge and security appliances like routers and firewalls, archives the obsolete perimeter model, and lets organizations shift from on-prem to cloud-based security and internetworking solutions.
To simplify: SASE uses a software-based virtual network to create regionally distributed points of presence (PoPs) that provide nearby secure networking and cloud-based security functions to branch offices and remote users. SASE brings security and networking geographically closer to users, cuts down lag and latency, eliminates the need for a company VPN, abolishes the obsolete perimeter model and lets organizations shift from on-premises to cloud-based security solutions. Rather than relying on the security of the data center, traffic from users’ devices gets inspected at a nearby PoP (the enforcement point) and sent onward from there.
SASE has several components:
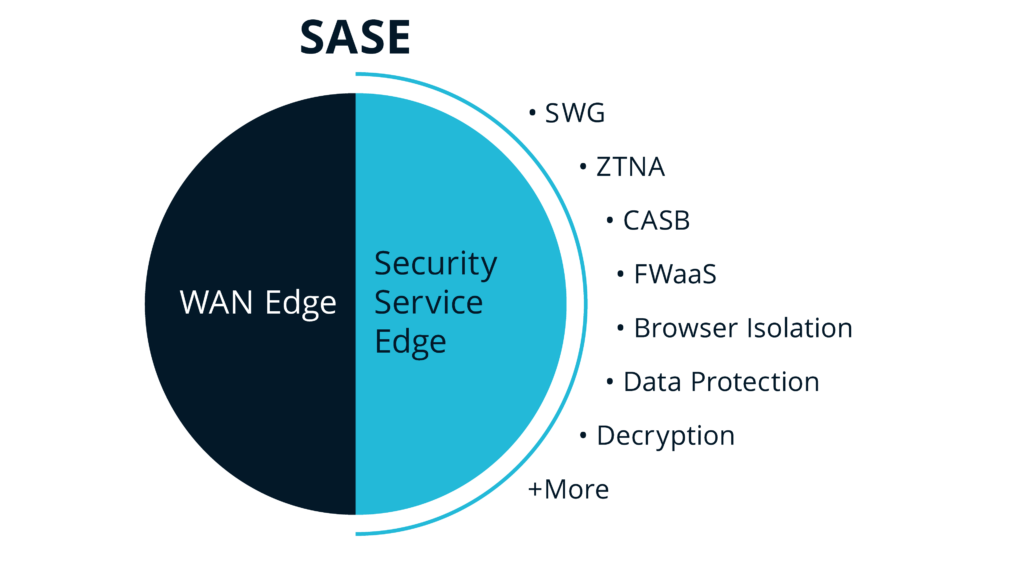
- CASB – Cloud access security brokers control traffic between the employees and company cloud instances and web applications. CASB can include access monitoring (IAM), endpoint detection and response (EDR) and data loss prevention (DLP).
- FWaaS – Cloud-based firewall-as-a-service filters network traffic according to the organization’s rules; can include next-gen (NGFW) functions like intrusion prevention/detection (IPS/IDS) or domain-name-system (DNS) security.
- SD-WAN – Software-defined wide-area networks securely link branch offices, data centers and remote users. The SD-WAN may overlay the public internet, may use a private backbone to link to PoPs—or both.
- SWG – Secure web gateways monitor, inspect and log users’ web traffic as well as blocking intrusions and malware. It can also filter content and block specific URLs according to organizational policy.
- ZTNA – Zero-trust network access verifies and authenticates each user upon access, regardless of user location. You can restrict lateral network movement with additional authorization requirements.
- Browser Isolation – protects users from untrusted, potentially malicious websites and apps by confining browsing activity to a secured environment that is separate from devices and networks.
- Data Protection – protecting sensitive information from damage, loss, or corruption.
And here comes SSE…
Two years after the initial SASE marketization, the team noticed another shift in corporate usage (namely, that many organizations weren’t adopting the SASE model). This trend led to Gartner defining SSE in 2021 as “securing service edge access to the web, cloud services and private applications…includ[ing] access control, threat protection, data security, security monitoring, and acceptable-use control enforced by network-based and API-based integration.”
SSE is SASE without the bulk of the SD-WAN, but still retaining the CASB, SWG, VPNaaS, and ZTNA functions: PoPs can be connected over the internet and enforced using the zero-trust policies instead of the SD-WAN. Many cloud-based companies simply don’t need SASE as SD-WAN is ideally suited for companies with both branch offices and remote workers.
What makes up the Security Service Edge
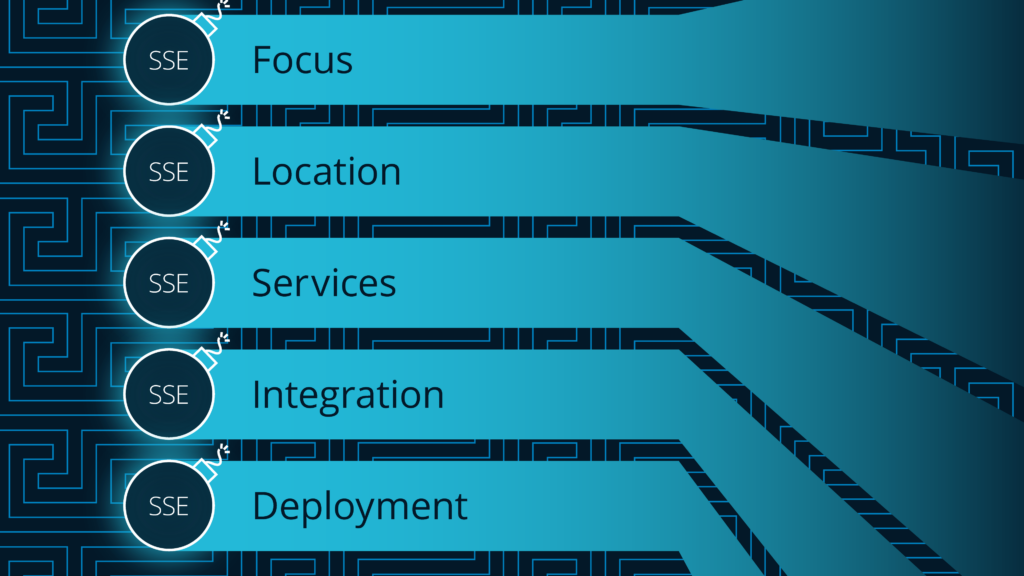
Focus: SSE primarily focuses on delivering security services for all traffic and resource access, while SASE is designed to provide edge networking, interconnectivity between all sites, and network security services to users accessing applications from anywhere in the world.
Location: SSE delivers security services at the edge of the network, which is typically the branch office or endpoint. SASE delivers connectivity and security services using a multi-tenant cloud.
Services: SSE provides a comprehensive set of security services, including ZTNA, VPNaaS, CASB, and SWG. SASE services include edge networking functionality such as FWaaS and SD-WAN, along with some less-frequently-used functionality such as remote browser isolation.
Integration: SSE is typically integrated with other security technologies, such as endpoint detection and response (EDR) and security information and event management (SIEM) systems. SASE is designed to be its own unified platform that provides multiple security and networking services, which often results in vendor lock-in.
Deployment: SSE is deployed more quickly (with the right product) and can overlay on top of existing edge and cloud networking products, while a SASE deployment may require multiple components (and a complete re-architecting of networks). SASE may also be deployed alongside other security platforms, assuming investment around integrating the tools.
A respondent to a 2022 Cyber Risk Alliance survey on cloud security said “my organization is most likely to consider purchasing an [SSE] solution that is a one-platform, comprehensive network security solution,” because this approach is more efficient and cost-effective than purchasing individual solutions for each aspect of network security. That sentiment seems to be reverberating throughout the industry, when 60% of companies recently chose SSE instead of SASE.
The post Secure Access Service Edge vs. Security Service Edge first appeared on Banyan Security.]]>Compare sitting at a desk today to sitting at a desk five or ten years ago; the way we work and access information has drastically changed. Employees may or may not be at their desks in a centralized office, working on desktop computers connected to a secure network. Instead, they work from multiple locations using a variety of devices to access resources. This shift in work culture has brought about the need for a new approach to network security – one that is device-centric.
What is Banyan’s device-centric approach?
Device centricity at Banyan refers to a security approach that focuses on securing the devices that access corporate resources, rather than securing the network itself. Closely related to user-centric security, this approach recognizes that today’s workforce uses multiple networks to connect to their resources: home networks, public Wi-Fi, and mobile networks. Focusing solely on securing the network misses the bigger picture and can leave the devices vulnerable to attacks.
By focusing on the device, security can be extended all the way to the resource, creating a more holistic approach to security. This approach considers the entire security landscape–from the device through to the resource–and ensures that security measures are in place at every stage of the process.
One of the biggest advantages of device-centric security: it makes connectivity more efficient. Instead of relying on a centralized network, connectivity is established between the device and the resource, regardless of the location. This means that employees can access resources quickly and efficiently, without the need for complex VPN configurations or slow connection speeds.
Device-centric security also provides better security outcomes. By focusing on the device, security measures can be tailored to each device and user, ensuring that they meet the specific security requirements of each resource. This approach enables organizations to implement posture verification, user verification, and intelligent routing, all of which contribute to better security outcomes.
Three Crucial Parts of Device-Centric Security
- Posture verification ensures that devices meet the minimum security requirements before being allowed to access corporate resources. This includes ensuring that devices have the latest security updates and patches, have anti-virus software installed, and are not jailbroken or rooted.
- User verification ensures that only authorized users can access corporate resources. This includes implementing multi-factor authentication and restricting access to resources based on user roles and privileges.
- Intelligent routing ensures that traffic is directed through the most secure and efficient route to the resource. This includes routing traffic through secure gateways and ensuring that sensitive data is encrypted.
Device-centric security is both a technical approach and a mindset about protecting the enterprise. The device accessing applications and resources becomes the commonality between breaching a corporate security posture and exploiting a resource. By focusing on the device, security can be extended all the way to the resource, creating a more holistic approach to security. This approach enables organizations to implement device identity and posture verification, user verification, and intelligent routing, all of which contribute to better security outcomes. By implementing device-centric security like Banyan’s security service edge, organizations can protect their employees while they access resources quickly and efficiently – ensuring that sensitive data is kept secure.
The post Device-Centric Security at Banyan first appeared on Banyan Security.]]>The CASB, or Cloud Access Security Broker, was born out of necessity in response to the rapid increase in use of cloud-based services and SaaS applications. Traditionally, organizations have protected their on-premises sensitive data with a combination of enterprise firewalls, identity, and access control solutions. However, those solutions can’t be used when the data lives in a third-party cloud, e.g., a SaaS application—especially when governed by policies that differ from one provider to another, and typically don’t satisfy an organization’s internal security requirements.
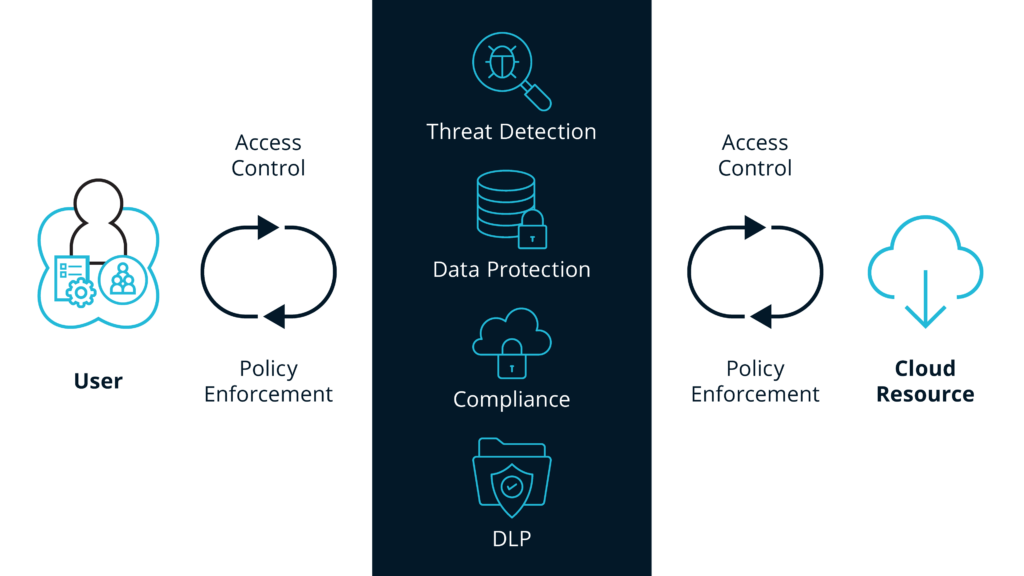
CASB addresses these challenges and more by proxying: being in the middle of the interaction between the end user and the cloud service, enforcing access and data protection policies and both ends of the transaction, making sure the user has the right privileges for the data they’re trying to access as well as ensuring that they are doing so in a secure fashion, preventing data loss and access to malicious actors.
CASB stands on four pillars – visibility, compliance, data security, and threat protection:
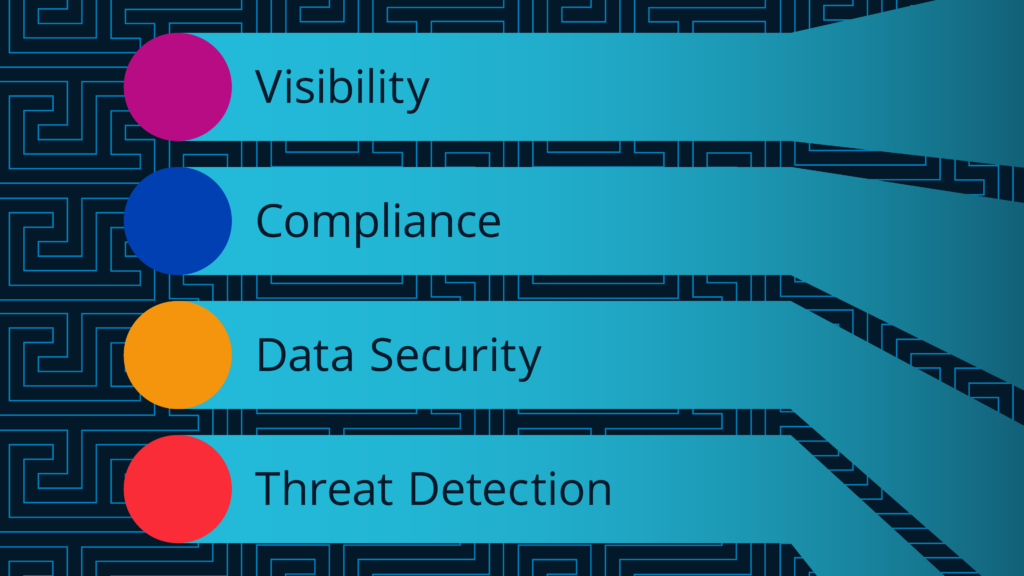
CASB provides visibility
Of major concern to organizations today is what is referred to as “shadow IT”, and the associated risks involved with BYOD use of cloud applications. Inadequate visibility and a lack of comprehensive audit logs often result in failure to comply with organizational security requirements. CASB capabilities often allow an organization to not only monitor access to the cloud resources but also act on potential threats and prevent unauthorized access.
CASB brings compliance
Many organizations must comply with regulatory and security guidelines like SOX, HIPAA, GDPR, and preserving PII of the users. CASB helps by encrypting data at rest and by automating reporting and auditing.
CASB helps data security
CASB provides the ability to monitor access to the organization’s sensitive data hosted in the third-party cloud services.
CASB provides threat protection
CASB protects the organization from potential threats and malware by analyzing and providing insights on malicious acts, based on the user and network behavior.
The Banyan cloud access security broker
CASB is an essential security component for any organization, providing a set of capabilities that allow organizations to monitor, manage, and prevent potential threats to their sensitive data. However, setting up and running a traditional CASB can be complicated and brittle, and doesn’t necessarily fulfill all of an organization’s security requirements.
Banyan Security’s modern take on CASB as part of our device-centric SSE (Security Service Edge) solution delivers a comprehensive view of the organization’s IT and security posture, with fine-grained access control and monitoring capabilities, focusing on usability and visibility while leveraging state of art technologies such as ZTNA (Zero Trust Network Access), VPNaaS (cloud-based VPN), and SWG (Secure Web Gateway) for holistic protection.
The post Four Advantages of a CASB first appeared on Banyan Security.]]>With IPSec, SSL, TLS, VPN, SDP, and ZTNA tunnels, it may sometimes become confusing to figure when to use which. IPSec was mostly used for site-to-site VPN and we’re going to focus on remote access. Clearly, there are different types of tunnels and different ways these tunnels are being configured.
With most organizations looking at Zero Trust Network Access (ZTNA), we’ll focus there specifically and do a quick comparison of first-gen ZTNA versus next-gen ZTNA like the Banyan Security Platform. First-gen ZTNA vendors like Zscaler incorrectly dismiss any type of tunnel. First-gen ZTNA is all about application access, which may be okay for most users in the organization. However, there will always be use cases where some type of tunneling is needed for super-users. For those organizations that move to a first-gen ZTNA vendor, they still need to have their legacy VPN running for these super users. The only other path these first-gen ZTNA vendors can offer is to make resources public-facing and hope for the best which is obviously not recommended.
Let’s look at the different ways these tunnels are typically employed. Workers commonly need to access internal applications, and often it’s a requirement that some of those workers are third-party contractors or vendors rather than employees. For third-parties especially, we want to make certain that the principle of least privilege is applied and the rules around their access are as narrowly defined as possible. For example, a manufacturing customer wanted to allow maintenance workers from their PLC (programmable logic controller) vendor Siemens to access their industrial automation system SIMATIC for a very specific amount of time during scheduled maintenance windows. Another use case is employees or third-parties accessing a specific module within a SaaS application. Again, first-gen ZTNA vendors handle this by making resources public-facing – a risky approach that Banyan would never recommend.
Why Banyan’s Tunnel is different
Banyan’s Service Tunnel is a modern approach which helps an organization quickly migrate away from legacy VPN or first-gen ZTNA while upgrading their usability and security at the same time. Let’s take a look at how:
- Discover and Publish – our solution finds all resources on-premises and in your cloud provider(s) allowing your IT team to quickly and easily create granular policies. This is especially important when going from full, layer 3 access to a zero trust model.
- Tunnel Discovery – this functionality also finds resources that are being accessed, however, this is specifically for traffic that is being tunneled. These resources may be those not deployed by central IT, but by specific lines of business. Again, once discovered, a policy can be published to lock down the tunnel further.
- Public domain support over Service Tunnel – when SaaS applications allow for source IP validation for connectivity, all traffic to that domain or SaaS application should be tunneled. This feature lets you quickly configure a domain and not worry about changing IP addresses or updating a list of hundreds of IPs globally. Ensure that only your authorized users are able to access third-party SaaS applications and your data.
- Decision-less access – unlike a VPN with many gateways, end users with Service Tunnel configured never have to decide which gateway to connect to. In fact, most of them may not know or even care about all the gateways. With a modern solution like Banyan’s, a single login allows your users to access authorized resources regardless of where they are or how you’ve deployed them. Your IT team can add sites without ever interrupting or needing to train your end user.
- Simple on-click access – users that are trying to optimize productivity want to get their work done quickly and without having to jump through hoops. With passwordless, stealth-mode access, the end user can do their job without having to first remember to enable the tunnel or connect to the right place. Imagine accessing a web application by just opening a browser and clicking on a bookmark. It really can’t get easier than that.
To learn more about upgrading and modernizing your legacy VPN, visit https://www.banyansecurity.io/vpn-replacement/.
The post Not All Tunnels Are Created Equally first appeared on Banyan Security.]]>Corporate employees are often required to do work that involves using publicly-accessible resources (e.g., Salesforce or a staging website), which go beyond the bounds of private network control. In light of the need to connect their workforce to these public SaaS applications, many organizations recognize the need for better security, visibility, and flexibility than legacy VPNs can offer. In other words, organizations want the security of a modern cloud VPN with continuous authorization throughout user sessions, as well as the flexibility for employees to work on public applications. So how can a Service Tunnel help?
This is where Banyan Security’s new cloud VPN feature comes in handy: Service Tunnel (our modern VPN as a Service) can now secure public resources based on domain or IP.

In this blog, we’ll explain how this works and how you can set up a Service Tunnel to provide your users a secure path to Salesforce.
The challenge
- Orgs require employees to use public resources (like Salesforce), but they have no way to ensure the security of their employees’ usage of these apps beyond the single authentication check that occurs during login.
- Lost or stolen credentials can be used to access public SaaS applications, putting the integrity and availability of sensitive organizational data at risk.
- Public SaaS apps have no authentication or continuous authorization built in; admins need to configure IDP integrations.
- Legacy IP whitelisting techniques require admins to manage large lists of continually changing employee source IPs.
Banyan’s Solution: Service Tunnel for Public Domains
In addition to routing traffic to your private networks, Service Tunnels can route public traffic destined for the internet. Internet traffic routed through Service Tunnel(s) uses the source IP of a Banyan Access Tier (the brain of Banyan’s product; a reverse proxy).
Admins can then IP whitelist to restrict user access on login and throughout a user’s session on a SaaS platform.
How to securely connect to Salesforce using Banyan
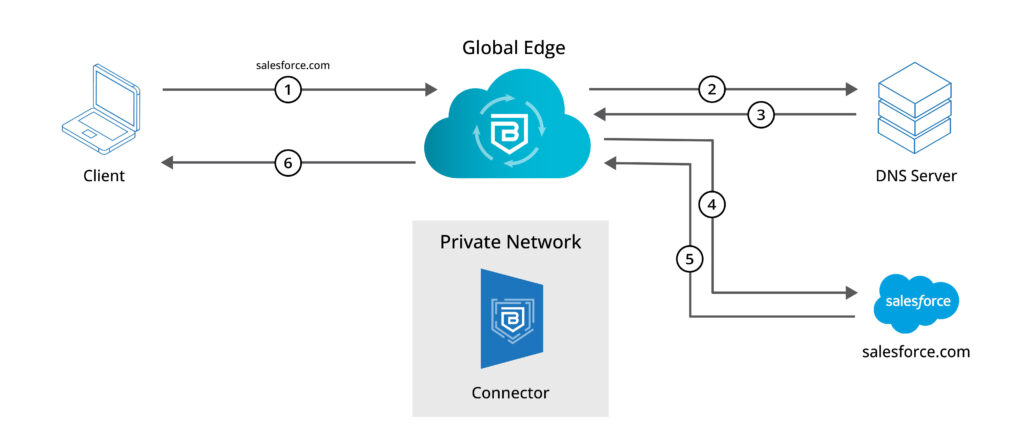
Here, we show how to use a Service Tunnel to route to multiple Salesforce subdomains:
- Register a Service Tunnel with Banyan, and configure it to route to public domains;
- Set IP whitelist rules for your users in Salesforce; and finally,
- Connect your Service Tunnel in the Banyan app, and securely access Salesforce.
For an in-depth guide on how to connect to a public SaaS service, like Salesforce, using Banyan, check out our Salesforce solution guide.
The post Secure Public Resources: Connect to Salesforce Using Banyan’s Service Tunnel first appeared on Banyan Security.]]>The evolution of the cybersecurity market has been to a great extent driven by the “arms race” between attackers and security professionals. Each iterative advance by one group has typically been met by a counter-response from the other that attempts to circumvent or neutralize the advances, and so on. Rinse and repeat. A similar cat-and-mouse dance has taken place with respect to user authentication and access controls.
For much of the history of modern computing, usernames and passwords have been — and remain — nearly omnipresent in the enterprise, even among those that have adopted stronger forms of authentication. One of the earliest efforts at thwarting passwords was the brute-force attack, and the inevitable — if not predictable — industry response was the shift to password rotation, as well as requirements for longer and more complex passwords that were harder to guess or crack. This response, however, added complexity and led to a painful user experience, for both admins and users. More to the point, the industry seems to have figured out that longer and more complex passwords and frequent rotation aren’t particularly effective at preventing credential abuse and attacks, so much so that the National Institute of Standards and Technology has recently stopped recommending the practice as part of its policy framework.
Once brute-forcing (and more complex passwords) reached the limit of its usefulness, the next phase was for attackers to “trick the human” by adopting phishing attacks or social engineering as a means to obtain valuable login credentials. And once again, the cybersecurity industry upped the ante, this time by adding more factors rather than more significant digits, including the use of SMS codes, one-time passwords (OTPs) or emails as an additional factor in two-factor authentication (2FA) and/or multi-factor authentication (MFA) schemes. Again, this led to an initial improvement in security, but also placed more of a burden on users and admins in terms of convenience, complexity, and overall user experience.
It’s no wonder, then, that passwords are still so commonplace in security, despite the fact that people have known of their many shortcomings for decades – the issue is that most MFA technologies have their own challenges, too, and it’s not always clear that the cure isn’t worse than the disease.
One of the more recent responses by the security industry has been “phishing-resistant” MFA. What does this mean? Phishing and its many variants – spear phishing, vishing, etc. – essentially try to trick users into clicking on a bad link or providing their login credentials. While many firms have tried to defeat phishing attacks by using MFA, not all forms of MFA are fully resistant to phishing attacks. Many types of authentication rely on some form of “shared secret” – such as a password, PIN, or one-time-password – that needs to be exchanged between users and the services they are attempting to access. However, shared secrets, regardless of form, are vulnerable to being intercepted at some point, potentially by a man-in-the-middle attack or other means.
Phishing-resistant MFA generally eliminates shared secrets, commonly by using a FIDO-based method or other approach that leverages public key cryptography and digital certificates. In such scenarios, users authenticate via a pair of public and private keys that are securely exchanged via asymmetric encryption without the risk of being intercepted. The added benefit of such an approach is that, done correctly, it potentially provides a more streamlined user experience as well as greater security — the “holy grail” of authentication.
However, as much as phishing-resistant MFA is a big step forward, it is limited to only verifying the user – it tells us nothing about the device that user may be attempting to log in with. By uniquely identifying the user’s device, the security bar can be raised significantly. Not only must users be authenticated, but so must the devices they are using. An attacker may have stolen a user’s credentials, but that person likely doesn’t also have physical possession of the device. Additionally, it’s important to understand the security posture of the device: Has it been rooted or jailbroken? Are patches up to date? Does it have malware on it, and is it a company-managed device or a personal device? Is there a way to separate personal from company data? And is company data encrypted? Those sorts of things are all important to know, and MFA alone can’t help there.
MFA also doesn’t help much if a user accidentally clicks on a bad link and inadvertently winds up at a bad website. For that reason, the organizations need industry to provide a solution that offers both device trust and URL filtering that can reduce the amount of damage that can happen when human beings are tricked into clicking on something or going somewhere they shouldn’t. This allows for better security AND better user experience, and it also lowers support costs/burdens.

Garrett Bekker III
Principal Research Analyst, Information Security at 451 Research, part of S&P Global Market Intelligence
@gabekker